If we use frida -U com.tencent.mm -l xxx or objection -g com.tencent.mm explore to hook directly, we can’t see the function call, because the process you hook is not the process of WeChat applet but the process of WeChat itself.
So we have to specify the pid to hook, we can use
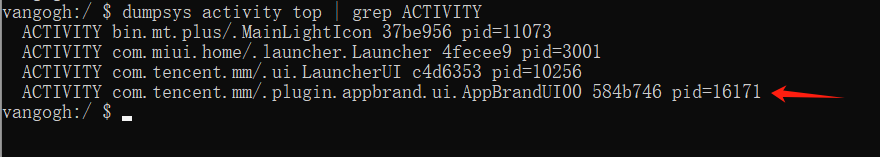
dumpsys activity top | grep ACTIVITY
to get it; we can also use frida -UF -l xxx to hook the current top-level Activity.
In order to reach the hook Wechat API, we need to locate the concrete JAVA class. Since we don’t know that yet, we can just make up a random class. And we will see the error.
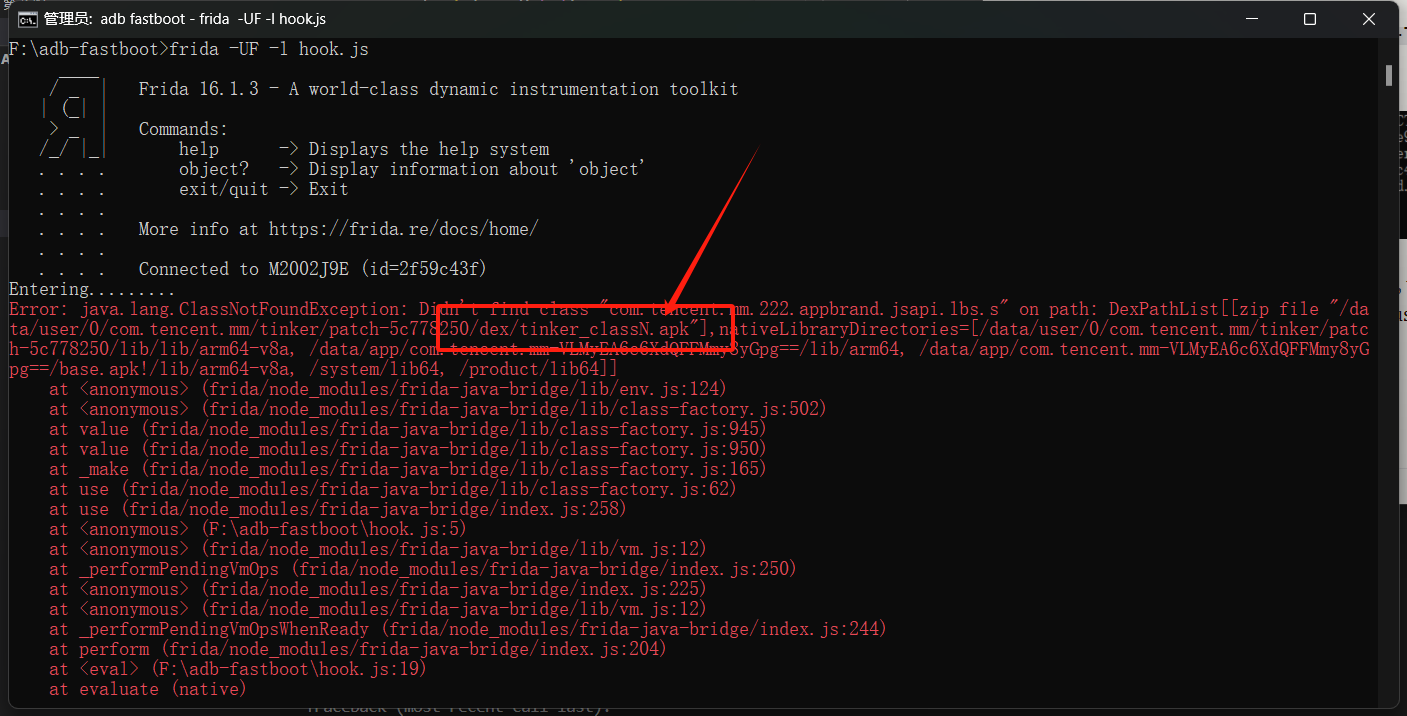
After that, we just need to look for it in the apk.
1 hook Miniapp API
Step 1 : Just hook the api when it is called
Java.perform(function () {
console.log("Entering.........");
// Hook wx.getLocation()
var getLocationClass = Java.use('xxx');
getLocationClass.x.overload('xxx', 'org.json.JSONObject', 'int').implementation = function (context, jsonObject, i15) {
console.log('getLocation called with data: ' + jsonObject.toString());
var result = this.x(context, jsonObject, i15);
return result;
};
});
This is a easy python script that we can use with all the proposed examples in this tutorial:
import frida, sys
with open(sys.argv[1], 'r') as f:
jscode = f.read()
pid = 16171
process = frida.get_usb_device().attach(pid)
script = process.create_script(jscode)
print('[ * ] Running Frida')
script.load()
sys.stdin.read()
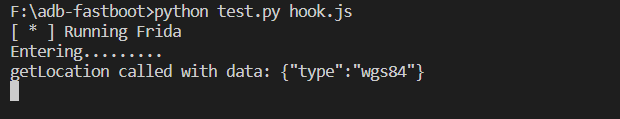
And we can see the prompt.
2 MiniApp API -> Android API
…continue


Meow, meowmeow, meow!